Follow the instructions below:
Outbound Open Ports:
Ports for data plane: Volumez needs to have outbound open ports from media to the application nodes, and from application to the media nodes, so that NVMe (port 8009) and/or iSCSI (port 3260) traffic can flow between applications and volumes.
There are no inbound connections required, to work with Volumez.
Ports for control plane: Volumez needs the outbound standard https port (443) to be open to volumez.com, so that the Volumez connectors can poll for orchestration commands from the Volumez service.
Inbound open ports:
Ports for data plane: Volumez needs to have inbound open ports from media to the application nodes, and from application to the media nodes, so that NVMe (port 8009) and/or iSCSI (port 3260) traffic can flow between applications and volumes. Inbound traffic is needed only locally between the instances inside your VPC.
For NVMe connectivity, you need to configure the AWS Security Group of the instances with inbound rules to open the Custom TCP port 8009 to the source 172.0.0.0/8.
For iSCSI, it is also possible to define connectivity by opening the Custom TCP port 3260 to the source 172.0.0.0/8.
Ports for management: In order to install the Volumez connectors, you need to have ssh access (port 22) to your application and media instances. There is no need for ssh access to the instances after the installation step, except for optionally performing troubleshooting operations.
Ports for control plane: Volumez does not require any inbound ports for its control operations.
Here is a sample list Inbound rules in a security group created for Volumez:
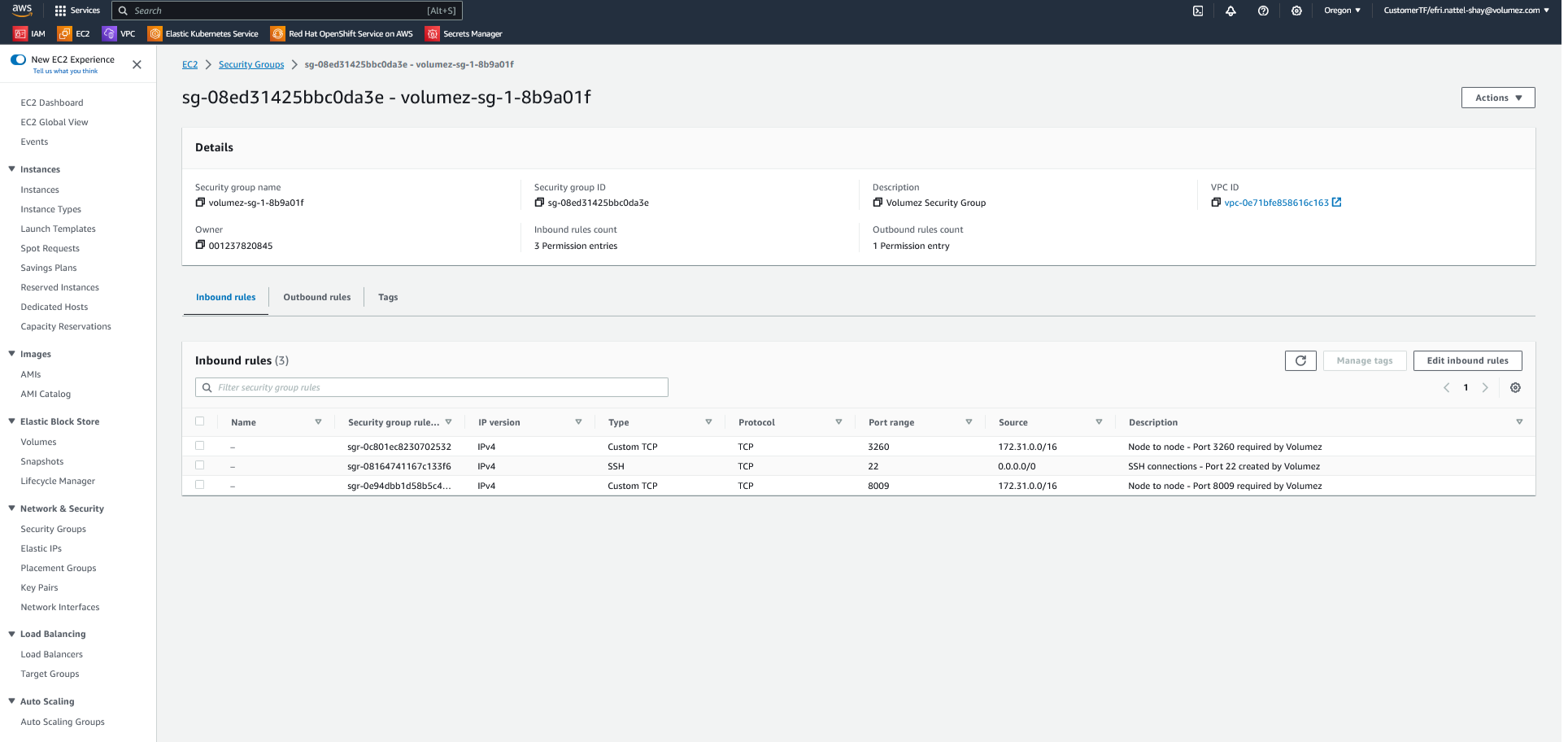
Cloud instances:
Application Nodes are cloud instances which run your applications. Each has a Volumez connector installed on it.
Volumez supports all AWS EC2 instances that run a supported operating system and contain NVMe.
Minimum requirements: 2 vCPU, 8 GB RAM.
AWS:
Supported EC2 types
App nodes
M *.large and up
C *.xlarge and up
R *.large and up
Media nodes
i*.large and up
c6gd.xlarge and up
Media Nodes are cloud instances that hold raw media (disks that the Volumez service uses to build logical volumes).
Media Nodes hold the data managed by the Volumez service to serve the Application Node requirements.
We recommend that you use Media Nodes that have only one SSD media. Having multiple media disks is supported, but media utilization and balancing the workloads across media may not be optimal. In addition, for optimal resiliency, using multiple instances with one disk in each instance is preferred over using fewer instances with multiple disks. Recommended nodes include:
AWS: is4gen.2xlarge, i4i.4xlarge, i3en.3xlarge
Smaller instances from these families are recommended only for lower capacity and performance requirements.
After you install a Volumez Connector on a cloud instance, you must assign it to operate as a Media Node.
IAM Role Permissions
To allow the Volumez service to create the required resources within your AWS environment, you must set up permissions in AWS Identity and Access Management (IAM).
Enable the following action in an IAM policy:
Resources: CrossAccountRole: Type: "AWS::IAM::Role" Properties: RoleName: "VolumezAutoProvisioningRole" AssumeRolePolicyDocument: Version: "2012-10-17" Statement: - Effect: Allow Principal: AWS: - "arn:aws:iam::225810133168:root" Action: - "sts:AssumeRole" Policies: - PolicyName: "VolumezAutoProvisioningEC2Policy" PolicyDocument: Version: "2012-10-17" Statement: - Effect: Allow Action: - ec2:UpdateSecurityGroupRuleDescriptionsIngress - cloudformation:CreateStack Resource: - "arn:aws:cloudformation:*:*:stack/volumez*" - "arn:aws:ec2:*:*:*/volumez*" - Effect: Allow Action: - ec2:CreateTags - ec2:CreateSecurityGroup - ec2:RunInstances - ec2:CreateLaunchTemplate - ec2:CreateLaunchTemplateVersion Resource: - "arn:aws:ec2:*:*:instance/*" - "arn:aws:ec2:*:*:security-group/*" - "arn:aws:ec2:*:*:launch-template*" Condition: StringEquals: aws:RequestTag/CreatedBy: - "volumez" - Effect: Allow Action: - ec2:CreateSecurityGroup - ec2:RunInstances NotResource: - "arn:aws:ec2:*:*:instance/*" - "arn:aws:ec2:*:*:security-group/*" - Effect: Allow Action: - ec2:AuthorizeSecurityGroupEgress - ec2:AuthorizeSecurityGroupIngress - ec2:DeleteSecurityGroup - ec2:TerminateInstances - ec2:RevokeSecurityGroupEgress - ec2:DescribeInstanceStatus - ec2:DescribeImages - ec2:RunInstances - ec2:CreateLaunchTemplateVersion Resource: - "*" Condition: StringEquals: aws:ResourceTag/CreatedBy: - "volumez" - Effect: Allow Action: - ec2:DescribeLaunchTemplateVersions - ec2:DescribeSecurityGroups - ec2:DescribeLaunchTemplates - ec2:DescribeRegions - ec2:DescribeAvailabilityZones - ec2:DescribeVpcs - ec2:DescribeInstanceTypes - ec2:DescribeSubnets - ec2:DescribeKeyPairs - ec2:DescribeTags - ec2:DescribeInstanceCreditSpecifications - ec2:DescribeInstances - ec2:DescribeInstanceAttribute - ec2:DescribeNetworkInterfaces - ec2:DescribeVolumes - ec2:DescribeLaunchTemplateVersions - cloudformation:GetResource - cloudformation:GetResourceRequestStatus - cloudformation:CreateResource - cloudformation:DeleteResource Resource: "*" Outputs: RoleARN: Description: "The ARN of the role that was created." Value: !GetAtt CrossAccountRole.ArnCreate an IAM role which is associated with these actions.
See more details here.
Setup guide : https://github.com/VolumezTech/volumez
AWS EC2 : EC2 ready for volumes
For Kuberentes check out this section