- 03 Jul 2024
- 1 Minute to read
- Print
- DarkLight
Technical Prerequisites
- Updated on 03 Jul 2024
- 1 Minute to read
- Print
- DarkLight
Follow the instructions below:
Outbound open ports
Ports for data plane: Volumez needs to have outbound open ports from media to the application nodes, and from application to the media nodes, so that NVMe (port 8009) and/or iSCSI (port 3260) traffic can flow between applications and volumes.
There are no inbound connections required, to work with Volumez.
Ports for control plane: Volumez needs the outbound standard https port (443) to be open to volumez.com, so that the Volumez connectors can poll for orchestration commands from the Volumez service.
Inbound open ports
Ports for data plane: Volumez needs to have inbound open ports from media to the application nodes, and from application to the media nodes, so that NVMe (port 8009) and/or iSCSI (port 3260) traffic can flow between applications and volumes. Inbound traffic is needed only locally between the instances inside your VPC.
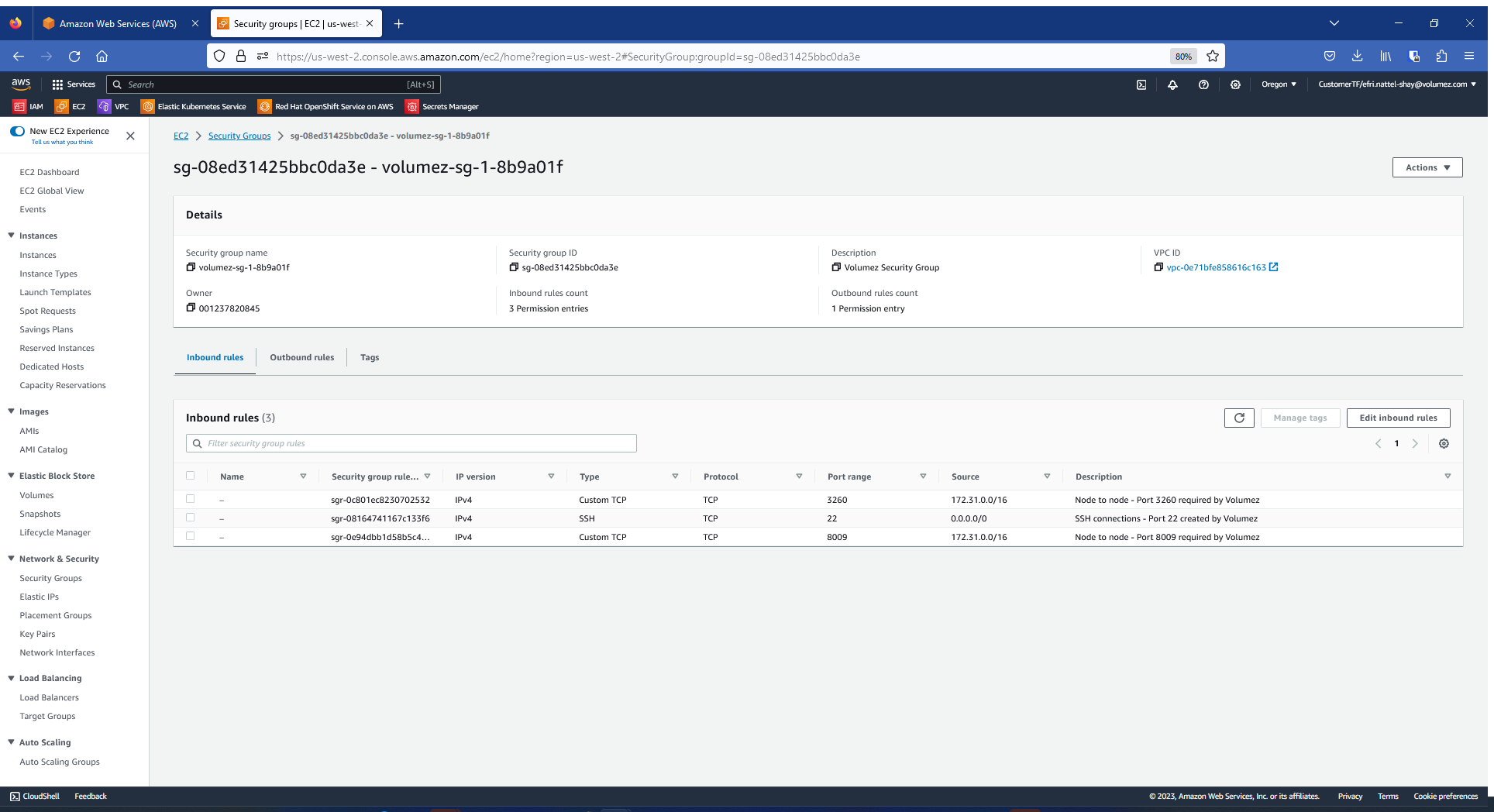
For NVMe connectivity, you need to configure the AWS Security Group / Azure Network security group of the instances with inbound rules to open the Custom TCP port 8009 to the source 172.0.0.0/8.
For iSCSI, it is also possible to define connectivity by opening the Custom TCP port 3260 to the source 172.0.0.0/8.
Ports for management: In order to install the Volumez connectors, you need to have ssh access (port 22) to your application and media instances. There is no need for ssh access to the instances after the installation step, except for optionally performing troubleshooting operations.
Ports for control plane: Volumez does not require any inbound ports for its control operations.
Here is a sample list Inbound rules in a security group created for Volumez:
Setup guide : https://github.com/VolumezTech/volumez
AWS EC2 : EC2 ready for volumes
Azure VMs: VMs ready for volumes
For Kuberentes check out this section